Why VAPT is Not Enough? The Need for External Attack Surface Management (EASM)
Vulnerability Assessment and Penetration Testing (VAPT) are essential, but alone, they cannot fully protect your business. Learn why EASM is critical for a comprehensive security strategy.
In today’s fast-paced digital landscape, businesses face increasing cybersecurity risks that can expose them to potential attacks. While Vulnerability Assessment and Penetration Testing (VAPT) are critical components of any security strategy, they are no longer enough on their own to fully protect your organization. At InOctal, we recognize that businesses need a more robust approach to defending against modern threats. This is where External Attack Surface Management (EASM) comes in.
The Limitations of VAPT
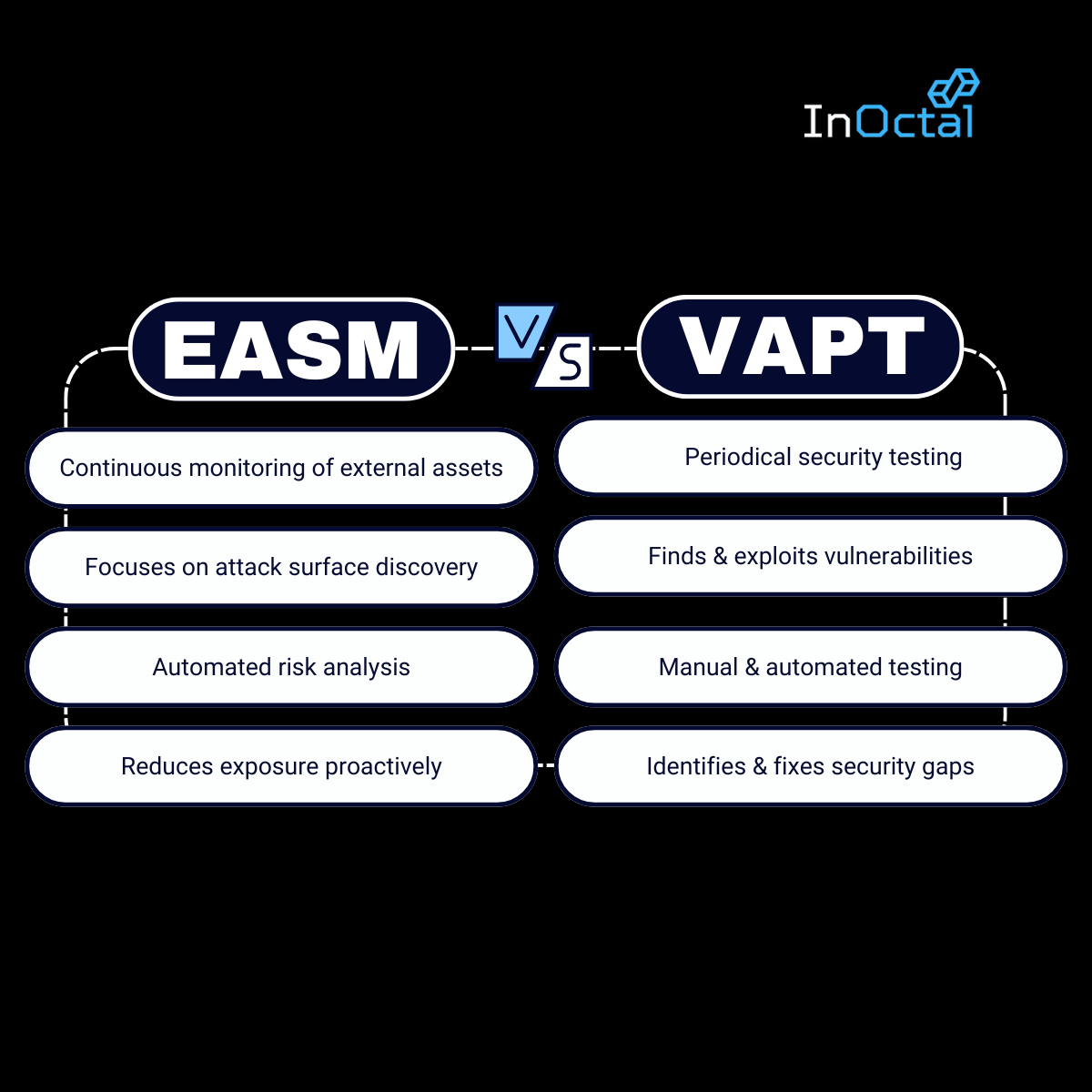
VAPT is a powerful combination of two key security practices: Vulnerability Assessment and Penetration Testing. VAPT helps organizations identify vulnerabilities and weaknesses in their systems and networks, as well as simulate attacks to understand how these vulnerabilities could be exploited by attackers.
What VAPT Can Do:
- Vulnerability Scanning: Identifies known security flaws in your infrastructure.
- Penetration Testing: Simulates real-world attacks to see how vulnerabilities can be exploited.
- Remediation Recommendations: Provides guidance on fixing vulnerabilities and improving security posture.
While VAPT is essential, there are several critical gaps that it cannot fill, particularly in today’s ever-evolving cyber threat landscape:
1. Incomplete Coverage of the Attack Surface
VAPT often focuses on internal systems or assets that are well-defined and controlled. However, modern businesses have an increasingly complex and dynamic attack surface that extends beyond traditional on-premise assets. Attack vectors such as shadow IT, third-party applications, and cloud-based infrastructures are typically not covered comprehensively during a VAPT assessment.
2. Limited Focus on External Threats
VAPT is typically an internal process. It may not adequately address the external vulnerabilities that can be exploited by attackers from the public internet. This leaves your business exposed to risks coming from external sources that are outside of the testing environment.
3. Reactive vs. Proactive Approach
VAPT tends to be reactive. It identifies vulnerabilities after the fact, meaning that any new threat or attack vector that emerges after the testing process might not be accounted for. Attackers are constantly evolving their tactics, and vulnerabilities change over time, making it difficult for traditional VAPT assessments to keep pace with the threats.
Why EASM is Critical for Continuous Security
External Attack Surface Management (EASM) is a proactive, continuous approach that helps businesses gain full visibility of their external attack surface, identify risks, and monitor new vulnerabilities in real-time. EASM focuses on the perimeter of an organization’s digital ecosystem, tracking all external-facing assets—whether on-premises, in the cloud, or with third-party vendors.
Key Benefits of EASM:
-
Comprehensive Coverage of the Digital Perimeter: EASM gives businesses complete visibility over their external assets, including third-party integrations, shadow IT, subdomains, cloud services, and more. It identifies assets that might be vulnerable but not part of the internal infrastructure covered by VAPT.
-
Continuous Monitoring and Threat Intelligence: Unlike VAPT, which is typically conducted on a periodic basis, EASM provides continuous monitoring. This ensures that you can detect emerging threats in real-time, enabling your organization to stay one step ahead of attackers.
-
Proactive Risk Identification: With EASM, vulnerabilities are discovered proactively as they emerge. This proactive approach helps your organization address potential weaknesses before they are exploited by attackers.
-
Third-Party Risk Management: Many organizations rely on third-party services, which can introduce vulnerabilities into your ecosystem. EASM helps you continuously track the security posture of third-party vendors and identify potential risks coming from these external sources.
-
Full Visibility into Shadow IT: Many businesses unknowingly use unapproved or unmanaged assets, known as shadow IT. EASM helps uncover these unknown assets, ensuring they’re included in your vulnerability management and risk assessments.

How EASM Complements VAPT
While VAPT is essential for identifying and mitigating vulnerabilities within an organization's infrastructure, EASM provides the broader visibility required to manage vulnerabilities across the entire digital landscape. Think of VAPT as a snapshot in time—important, but not comprehensive. EASM, on the other hand, is a continuous monitoring solution that detects emerging threats and vulnerabilities across all your external-facing assets.
Together, VAPT and EASM create a robust, layered security strategy that helps businesses defend against external and internal threats, ensuring both immediate and ongoing protection.
Why VAPT Alone Isn’t Enough
While VAPT helps identify security weaknesses and prevent attacks, it has several key limitations in today’s fast-changing threat landscape:
-
Misses External-facing Assets: VAPT typically focuses on internal systems and misses the external attack surface—potentially exposing businesses to risks from third-party applications, subdomains, and cloud environments.
-
Static and Periodic: VAPT assessments are usually conducted at regular intervals, but cyber threats evolve continuously. Attackers are always looking for new ways to exploit vulnerabilities that may have been overlooked in the last test.
-
Lack of Visibility into Emerging Risks: New technologies, cloud services, and third-party integrations can introduce new vulnerabilities. VAPT cannot track these constantly changing elements in real-time like EASM can.
-
Shadow IT: Employees may unknowingly introduce insecure devices, apps, or services into the organization, creating vulnerabilities. VAPT does not typically include this type of risk.
How InOctal’s EASM Solution Protects Your Business
At InOctal, our EASM solution is designed to give businesses the visibility and intelligence they need to stay ahead of threats. We continuously monitor your external attack surface and provide actionable insights to help mitigate risks before they become vulnerabilities.
Why Choose InOctal's EASM:
- Comprehensive Visibility: Gain a complete view of your external attack surface, including third-party services, subdomains, cloud infrastructures, and shadow IT.
- Continuous Risk Monitoring: Receive real-time updates and alerts about emerging threats, ensuring you can act quickly to mitigate risks.
- Seamless Integration: Our EASM platform integrates seamlessly with your existing security tools, providing an additional layer of protection without disrupting your current workflows.
- Proactive Defense: Stay ahead of potential vulnerabilities by proactively identifying risks before they can be exploited by attackers.
In conclusion, while VAPT is an important part of your cybersecurity strategy, it is no longer enough on its own. With the rise of sophisticated cyber threats, businesses must adopt a proactive approach to security. External Attack Surface Management (EASM) provides continuous monitoring, proactive risk identification, and a comprehensive view of the external-facing assets that could be exploited by attackers. By integrating EASM with VAPT, organizations can ensure robust protection and mitigate potential vulnerabilities across their entire digital ecosystem.
Ready to Protect Your Business with EASM?
Contact InOctal today to learn more about our External Attack Surface Management (EASM) solutions and how we can help you stay one step ahead of cyber threats.
Get in touch: info@inOctal.com