What is Vulnerability Assessment & Penetration Testing?
Vulnerability Assessment and Penetration Testing (VAPT) are two key practices in cybersecurity that help identify and mitigate security threats.
In the ever-evolving world of cybersecurity, ensuring the security of your applications, networks, and infrastructure is paramount. One of the most effective ways to protect your digital assets is through Vulnerability Assessment and Penetration Testing (VAPT). These two practices are widely used to identify weaknesses, strengthen defenses, and proactively prevent cyberattacks. At InOctal, we specialize in providing comprehensive VAPT services to safeguard businesses from potential cyber threats.
What is Vulnerability Assessment?
Vulnerability Assessment is the process of identifying, quantifying, and prioritizing vulnerabilities in a system, network, or application. The goal is to find flaws or weaknesses that could be exploited by attackers before they can cause harm. Vulnerability assessments are typically automated using specialized tools that scan and identify potential vulnerabilities.
Key Steps in Vulnerability Assessment:
- Discovery: Identifying assets in the network or system that need to be assessed.
- Scanning: Using vulnerability scanners to check for known vulnerabilities, misconfigurations, and security gaps.
- Analysis: Evaluating the severity and impact of the vulnerabilities found.
- Reporting: Compiling a comprehensive report outlining the findings and recommendations for remediation.
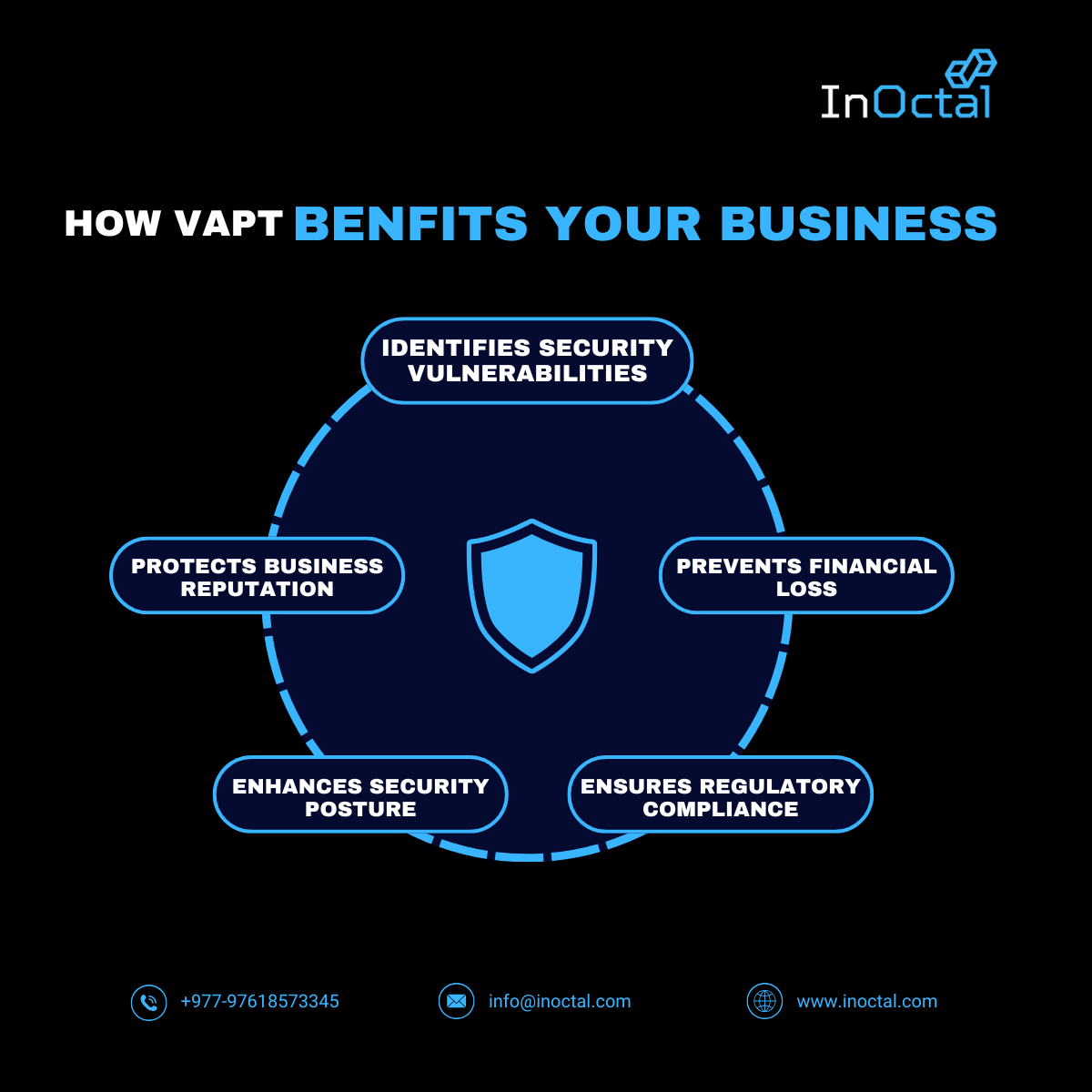
Benefits of Vulnerability Assessment:
- Helps to identify known vulnerabilities and misconfigurations.
- Allows organizations to patch vulnerabilities before they are exploited.
- Helps prioritize remediation based on risk levels.
What is Penetration Testing?
Penetration Testing (Pen Testing) is a simulated attack on a system, application, or network designed to identify vulnerabilities that could be exploited by cybercriminals. Unlike vulnerability assessments that identify potential weaknesses, penetration testing goes one step further by attempting to exploit those vulnerabilities, providing a realistic view of what could happen if an attacker were to exploit a weakness.
Key Steps in Penetration Testing:
- Planning: Defining the scope, objectives, and rules of engagement for the test.
- Information Gathering: Collecting information about the target system to identify potential vulnerabilities.
- Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access.
- Post-Exploitation: Assessing the impact of a successful attack, including lateral movement and data exfiltration.
- Reporting: Providing detailed documentation of findings, including discovered vulnerabilities, exploited issues, and recommended remediation steps.
Benefits of Penetration Testing:
- Provides a real-world view of how an attacker could breach your system.
- Helps identify weaknesses that automated scanners might miss.
- Tests the effectiveness of existing security controls.
Why Both Vulnerability Assessment & Penetration Testing Matter?
While Vulnerability Assessment identifies known vulnerabilities and security gaps, Penetration Testing mimics an actual attack to test how those vulnerabilities could be exploited. Together, these practices provide a comprehensive approach to cybersecurity by not only identifying weaknesses but also testing them to determine their potential impact.
The Synergy of VAPT:
- Proactive Defense: Both VAPT practices help prevent attacks by identifying and fixing vulnerabilities before they can be exploited.
- Improved Security Posture: Regular assessments and testing ensure that your security measures evolve with emerging threats.
- Risk Management: By understanding the vulnerabilities and the extent of potential damage, businesses can better manage cybersecurity risks.
How InOctal Can Help?
At InOctal, we specialize in delivering world-class Vulnerability Assessment & Penetration Testing (VAPT) services to help organizations safeguard their digital infrastructure. Our experienced cybersecurity experts follow industry best practices to identify vulnerabilities, test the security of your systems, and provide actionable insights for improving your defenses.
We utilize the latest tools and techniques to ensure thorough and effective assessments, providing you with the peace of mind that your systems are secure. Whether you’re a small business or a large enterprise, our customized VAPT solutions are designed to meet your specific needs.
Reach out to us today to schedule a consultation and take the first step in securing your business against cyber threats!
Contact us: info@inOctal.com
Feel free to reach out for a personalized consultation or with any questions!